What Are AWS Trusted Advisor Checks?
In simple terms, AWS Trusted Advisor is a native AWS tool that provides active guidance to operate AWS workloads consistently, safely, and efficiently.
AWS Trusted Advisor acts as a consultant with deep knowledge of AWS who can diagnose problems within your AWS infrastructure to improve performance, reliability, security, and costs. AWS Trusted Advisor evaluates your AWS resources by using pre-defined monitoring rules called “Checks.” Checks identify ways to optimize AWS services and resources in five categories:
- Cost Optimization
- Performance
- Security
- Fault Tolerance
- Service Limits
Not all Checks are available to every account. AWS has set up a pricing plan to offer more Checks to customers subscribing to a higher support plan. The table below describes the Checks available under each type of AWS Support Plan:
| Basic and Developer Support | Business Support | Enterprise Support | |
|---|---|---|---|
| Cost Optimization | Not available | All checks are available | All checks are available |
| Performance | Not available | All checks are available | All checks are available |
| Security | Only Core Security Checks are available | All checks are available | All checks are available |
| Fault Tolerance | Not available | All checks are available | All checks are available |
| Service Limits | All checks are available | All checks are available | All checks are available |
AWS Trusted Advisor Pricing Plans (Table 1.1)
We have organized this article into multiple sections for the sake of clarity.
We’ll first present the basic concepts behind the AWS Trusted Advisor. Next, we’ll present a few popular Checks in each category. We will then explore how these Checks show their output on the AWS Trusted Advisor Dashboard. Towards the end of the article, we will discuss a few limitations of the AWS Trusted Advisor service. Finally, we wrap this article by introducing two integrations between AWS Trusted Advisor and other complementary AWS services.
Let’s get started with AWS Trusted Advisor.
Getting Started with AWS Trusted Advisor
This section is solely for the beginners who are new to AWS Trusted Advisor or for the readers who need a refresher on the basic concepts. We will quickly review how AWS Trusted Advisor works and then explore how to view Dashboard and Check Categories in the AWS Console. If you are exclusively interested in learning about essential Checks and their applications, skip this section.
Through Checks, AWS Trusted Advisor examines your AWS services and resources and compares them to the AWS best practices spanning five categories. Based on Checks’ results, AWS Trusted Advisor recommends actions that you should take to optimize your infrastructure.
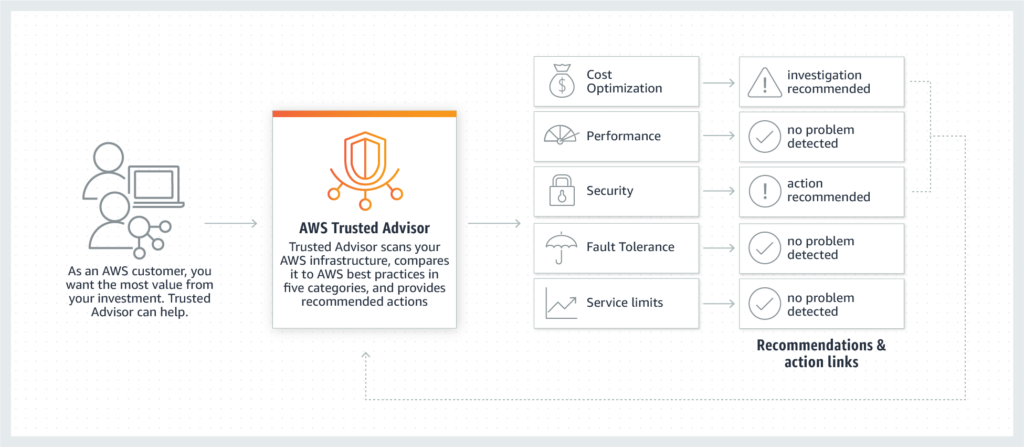
Workflow of AWS Trusted Advisor – Figure 1.1 (source)
AWS Trusted Advisor Console
AWS Trusted Advisor console provides a summary of the results of the Checks. You can sign in to the AWS Management Console to access the AWS Trusted Advisor console.
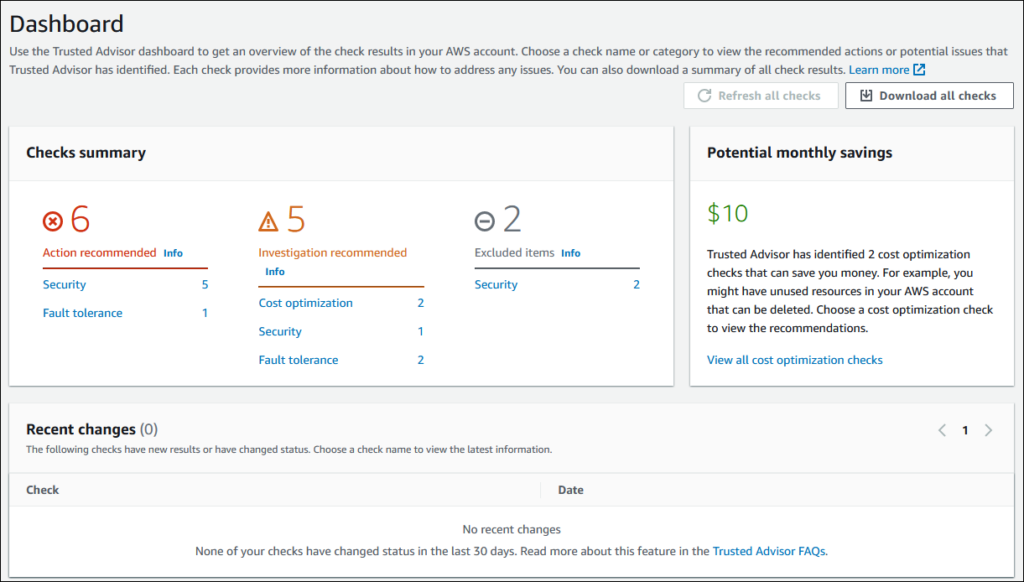
1. Dashboard
The dashboard presents the overall summary of the Checks’ results. For example, the screenshot below shows six recommended actions, five suggested investigations, and two items that are excluded.
- Recommended Actions: denoted in red.
- Investigation: potential issues shown in yellow.
- Excluded: resources that are excluded (un–scanned) presented in the color gray.
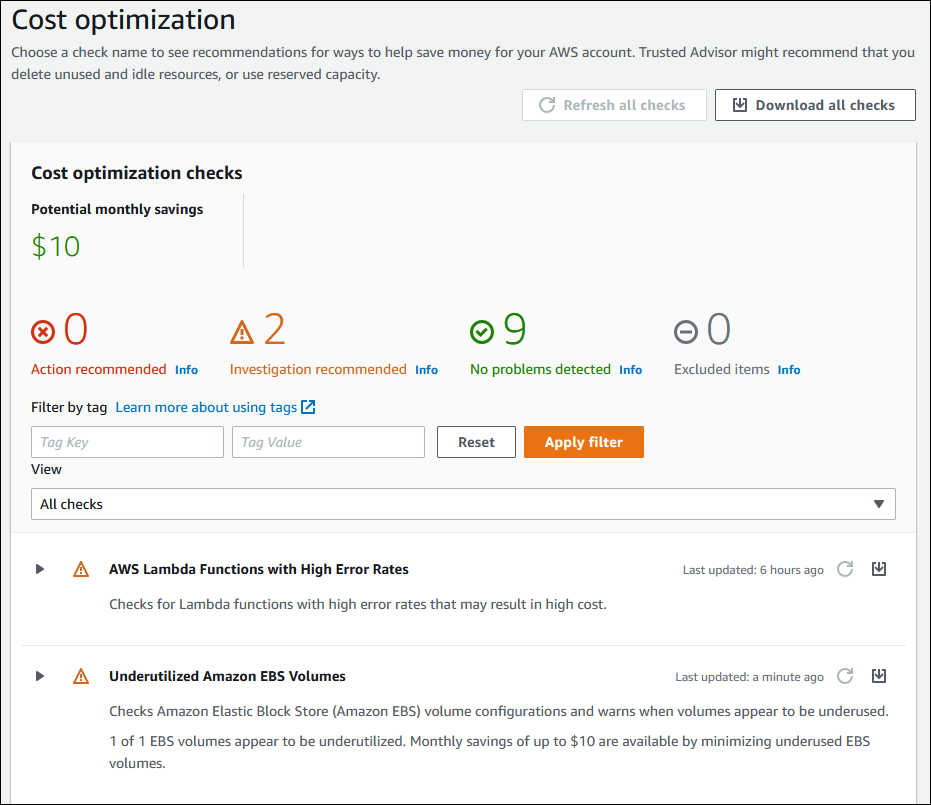
2. Checks Categories:
AWS Management Console shows five Checks categories: Cost Optimization, Performance, Fault Tolerance, Security, and Service Quotas. You can click each category to have a detailed view of recommended actions and specific checks. For instance, if you drill down into the Cost Optimization Category, you can see a screen similar to the one below:
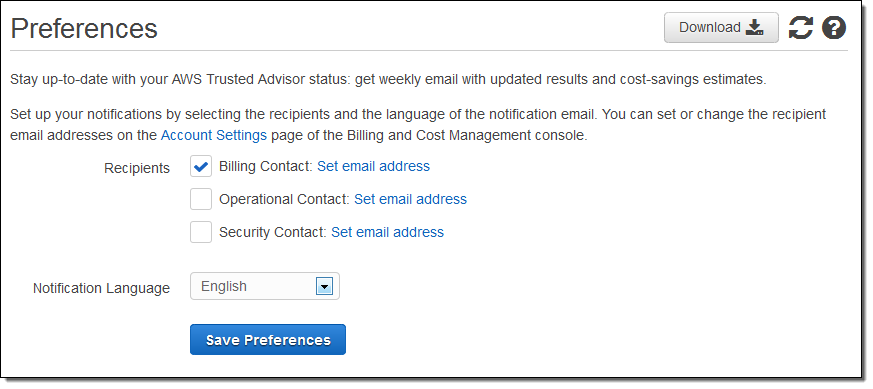
Notifications
Notifications provide updates about the results of the Checks and show the cost-saving estimates. We’ve taken the below image from AWS official documentation to show you what the “Preferences” section looks like.
If you need additional information on the basic concepts of AWS Trusted Advisor, you can browse the AWS Official Guide.
AWS Trusted Advisor Checks
Checks are the mechanisms through which Trusted Advisor keeps an eye on your AWS resources. At the time of this article’s writing, AWS offers:
- 20 Checks in the Cost Optimization Category.
- 11 Checks in the Performance Category
- 20 Checks for Security including 6 Core checks
- 23 Checks are available under Fault Tolerance
- 52 Checks are under Service Limits.
We will only discuss the following popular Checks in each category:
| Category | Check’s Name |
|---|---|
| Cost Optimization | Amazone EC2 reserved instance optimization Amazon RDS Idle database instances AWS Lambda functions with excessive timeout Idle load balancers Unassociated elastic IP addresses |
| Performance | Large number of EC2 security group rules applied to an instance Overutilized Amazon EBS magnetic volumes CloudFront content delivery optimization |
| Security | MFA on root account Security groups with specific ports unrestricted Amazon S3 bucket permissions Amazon RDS public snapshots IAM use |
| Fault Tolerance | Amazon EBS snapshots Amazon S3 bucket versioning Load balancer optimization Amazon RDS backups |
| Service Limits | SES daily sending quota RDS total storage quota EC2 reserved instances quota CloudFormation stacks |
Cost Optimization Checks
A considerable percentage of money is wasted on unused AWS services or resources because we provision more capacity than required by our applications. Below are ten operational tasks that require regular upkeep:
- Rightsizing EC2 Instances
- Scheduling on/off times
- Purchasing Reserved Instances
- Delete unattached EBS volumes
- Delete obsolete snapshots
- Release unattached Elastic IP addresses
- Upgrade instances to the latest generation
- Purchase reserved nodes for Redshift and ElastiCache Services
- Terminate zombie resources
- Move infrequently-accessed data to lower-cost tiers
Sounds daunting? An easier approach is to enable Cost Optimization Checks from your AWS Trusted Advisor Console.
With the 20 Checks under the Cost Optimization category, you can weigh the status provided against your requirements and then act on or ignore the suggestions.
1. Amazon EC2 Reserved Instance Optimization: This Check helps reduce the costs incurred from using On-Demand Instances.
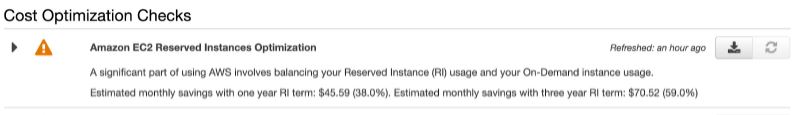
For all Jerry Maguire fans (“Show me the money!”) – you can save $45.59 with a one-year Reserved Instance term and $70.52 with a three-year Reserved Instance term. That’s a saving of 38 % and 59%, respectively.
2. Amazon RDS Idle DB instances: Anything inactive in your AWS infrastructure adds more to your AWS costs and should be removed. This Checkidentifies idle Amazon RDS database instances and deletes them to reduce your AWS bill. To get the information on Idle RDS DB instances,you can either use AWS Trusted Advisor console and enable the Check with the given name or use the below code snippet (AWS Support API):
import boto3
import csv
support_client = boto3.client('support')
csv_file = open('all_idle_rds.csv', 'w')
obj = csv.writer(csv_file, delimiter=',')
idle_rds_check_id = ''
checks_response= support_client.describe_trusted_advisor_checks(language='en')
for check_detail in checks_response['checks']:
if check_detail['category'] == 'cost_optimizing' and
check_detail['name'] == 'Amazon RDS Idle DB Instances':
idle_rds_check_id = check_detail['id']
csv_header = check_detail['metadata']
obj.writerow(csv_header)
get_check_result=
support_client.describe_trusted_advisor_check_result
(
checkId=idle_rds_check_id,
language='en'
)
for idle_rds in get_check_result['result']['flaggedResources']:
obj.writerow(idle_rds['metadata'])
AWS Support API(source)
3. AWS Lambda functions with Excessive timeouts: Lambda charges based on run time and the number of requests. Excessive timeouts lead to a more significant number of Lambda requests and the total execution time. This Check identifies Lambda functions with high timeout rates, potentially saving your AWS bill.
4. Idle Load Balancers: Load Balancers distribute your incoming traffic across multiple targets. This Check will scan your idle CLBs’(Classic Load Balancers) configuration and return a Yellow flag if the Load Balancer is not active or a Red Flag if the Load balancer is not associated with any back-end instance.
5. Unassociated Elastic IP Addresses: There is no cost for Elastic IP addresses when in use. However, AWS will bill you for unused Elastic IP addresses associated with your AWS account. The charges are nominal but still add to your usage cost. This Check will alert you whenever it detects an unused Elastic IP in your AWS infrastructure.
Performance Checks
Accept that we all are consumed with the performance and capacity of our systems. This category is more focused on the performance of your applications. The Checks in this category ensure optimal utilization of our resources. We have already mentioned some of the significant checks in table 1.1. Let’s dive into the Checks in serial order.
1. Large Number of EC2 Security Group Rules Applied to an Instance: A large number of security group rules hinders the performance of an EC2 instance. This Check identifies such an occurrence. Have a look:
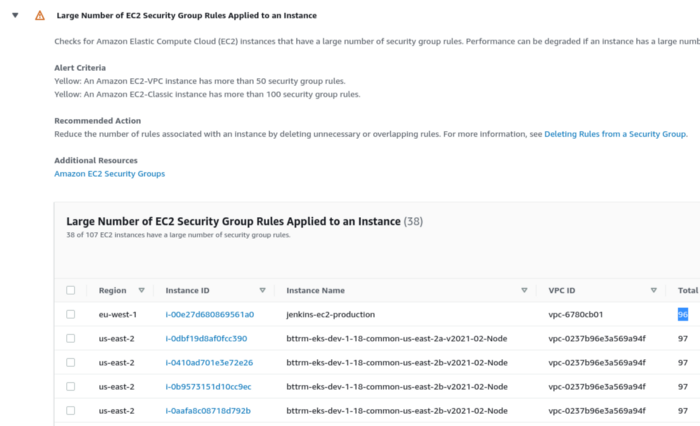
Did you see how this Check recommends an action to reduce security group rules of EC2 instances (such as Jenkins EC2 instances) as this could degrade performance?
2. Overutilized Amazon EBS Magnetic Volumes: checks for AWS EBS magnetic volumes that are potentially overutilized and might benefit from a more efficient configuration.
3. CloudFront Content Delivery Optimization: This is a valuable Check to evaluate any scope of accelerating data transfer from the S3 bucket by using AWS CloudFront.
Security Checks
The most sensitive task is to avoid security exposures. You should always follow AWS Best Practices for Security to secure your AWS infrastructure from external threats. An AWS Trusted advisor adds another layer of security by ensuring that your applications are not exposed to vulnerabilities.
- MFA on Root Account: Multi-factor authentication (MFA) is always recommended for better security. This Check gives a warning if MFA is not enabled on the root account.
- Security Groups – Specific Ports Unrestricted: If you do not restrict access to your ports, you will be exposed to Denial of Service (DoS) Attacks, loss of data, or hacking. This Check verifies security groups and their inbound rules for IPv4 addresses.
- Amazon S3 Bucket Permissions: This evaluates explicit bucket permissions and bucket policies for any open permissions or access.
- Amazon RDS Public Snapshots: RDS takes Snapshots of Storage Volumes of your DB instances and stores them to AWS S3. The public access of snapshots is a major threat to cloud security. This Check alerts users if any snapshot is configured in a way that makes it publicly accessible.
- IAM Use: Alerts you if you’ve created users, groups, and roles to control access to your AWS resources rather than using your account credentials.
Let’s take a look at a Security Category snapshot below:
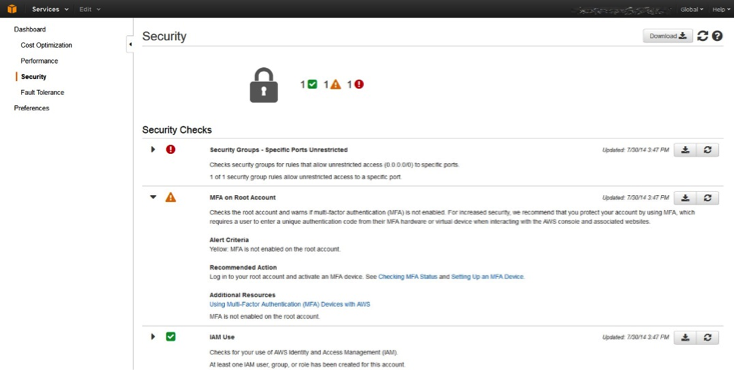
You can see one green checkmark icon; the number 1 next to this icon indicates that there has been one successful Security Check and that no action is needed for this item. You can also see a red exclamation point icon with the number 1. It shows that there is one security item that needs attention.
An example shows that specific ports are unrestricted. If you expand the issue, AWS will provide information on how to resolve the issue. Once you’ve fixed the problem, click the refresh button against the Check so that AWS can recheck the issue and confirm its resolution.
Fault Tolerance Checks
Fault tolerance Checks are designed to keep your applications running with zero downtime. Let’s drill down into the checks that maintain this crucial service level goal.
Amazon EBS Snapshots: This Check is similar to the “Amazon RDS Public Snapshots” Check under the Security Check category and is designed to help prevent breach of data security by alerting users when an EBS snapshot is publicly accessible.
- Amazon S3 Bucket Versioning: Versioning keeps multiple versions of the same object in the same bucket to help restore older versions when necessary. This check examines if the S3 bucket has versioning enabled or suspended.
- Load Balancer Optimization: Theoretically,there should be an equal number of instances across multiple Availability Zones for the Elastic Load Balancers to work effectively. This Check evaluates the configuration of the Load Balancers and reports if they are working optimally or not.
- Amazon RDS Backups: AWS enables RDS backups by default for potential recovery. If we mistakenly set the current value for the retention period to 0 (zero), then AWS RDS will no longer take snapshots for that particular instance. This check confirms that RDS backups remain enabled.
Service Limits Checks
AWS has placed limits or quotas on the number of services and resources you can provision at any given point in time. For example, Amazon Simple Email Service (SES) limits sending emails to only 200 per day for a sandbox account. The Checks in the Service Limits Category are meant to notify users when usage of a given service nears its limit. Amazon now covers 12 AWS services in this Category:
- EC2 instances
- DynamoDB
- EBS
- RDS
- VPC
- Route 53
- Auto-Scaling Group
- Elastic Load Balancers
- IAM
- CloudFormation
- SES
- Kinesis
You can see a sample AWS Trusted Advisor Dashboard for EC2 service limits in a single AWS region.
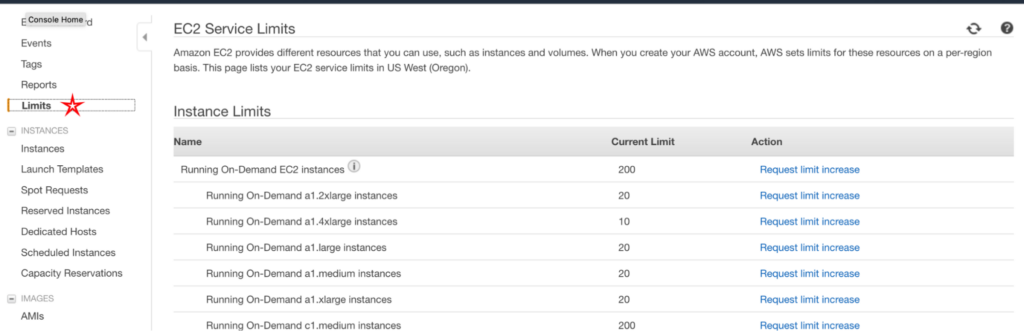
- ES Daily Sending quota: checks if the usage is beyond 80% of the SES Daily quota.
- RDS Total Storage quota: checks for usage that is more than 80% of the RDS total storage quota.
- EC2 Reserved Instances quota: checks for usage that is more than 80% of the EC2 Reserved Instance leases quota.
- CloudFormation Stacks: checks if the usage exceeds 80% of the CloudFormation stacks quota.
Working through AWS Trusted Advisor Checks Limitations
AWS Trusted Advisor has some limitations. Knowing them beforehand will help you work around these issues and leverage third-party tools in conjunction. Let’s review them.
- Advanced Analytics: AWS Trusted Advisor Checks are analyzed within a silo (of performance or security) and based on rules as opposed to machine learning technology. As such, the checks don’t correlate events across platforms nor apply algorithms to de-duplicate redundant events. This functionality requires feeding the output of the checks to a third-party event correlation engine.
- Lack of automated actions: AWS Trusted Advisor Checksnotify users of a problem but don’t take actions to fix them. There are no automated actions associated with the recommendations to resolve them unless you write custom code and trigger it as a Lambda function which is too complex for the average user.
- No Custom Checks: AWS has a set of pre-designed Checks spanning five categories. You cannot create custom Checks unless they are predefined by AWS.
- AWS only. Trusted Advisor Checks are available only for AWS, which is not ideal for companies that operate multi-cloud and hybrid cloud environments.
Integrations with other AWS services
AWS CloudWatch
You can integrate AWS CloudWatch with AWS Trusted Advisor since Trusted Advisor publishes metrics for all checks to CloudWatch. You can also create custom alarms to understand the number of resources scanned by each Check. One of the exciting applications of both services working together is to manage your AWS deployments by monitoring Service Limits with the help of AWS CloudWatch. You can go through the Service Limits and CloudWatch if you are interested in pursuing this functionality.
Amazon QuickSight and Amazon Athena
This module is for you if you are a statistics aficionado. You can use Amazon Athena to analyze your data by running queries and using Amazon QuickSight to visualize the results of those queries.
A discussion about the techniques for integrating these services is outside of our article’s scope, but you can find out more about QuickSight and Athena on the AWS website.
Conclusion
AWS Trusted Advisor provides helpful information about your AWS infrastructure on topics related to cost, performance, security, fault, and quotas. Companies that operate hybrid and multi-cloud environments can overcome the shortcomings by feeding the notifications generated by Trusted Advisor to OpsRamp’s incident management platform that is powered by machine learning and a policy engine to correlate the notifications with other relevant events from various public and private cloud sources. The resulting enriched and accurate events can then feed OpsRamp’s automation engine to take remedial action without the need for error-prone or delayed human intervention.
You like our article?
Follow our monthly hybrid cloud digest on LinkedIn to receive more free educational content like this.