It’s no secret that network security is a fundamental requirement for modern cloud workloads. However, it can be hard to determine the best security for a specific use case with all the different security appliances and tooling available. For example, Azure Firewall and Azure Network Security Groups (NSG) are two popular security solutions for Azure cloud workloads, but they serve significantly different purposes.
In this article, to help you expand your Azure security knowledge, we’ll explore Azure Firewall vs. NSG in depth. In addition to comparing Azure Firewall and NSG features, we’ll drill down and take a look at use cases so you can decide which solution is best for your requirements.
What is Azure Firewall?
Azure Firewall is a cloud-based fully-managed intelligent firewall that protects workloads from OSI layer 3-7.
Azure Firewall goes beyond the classic security approach of authorization based on IP, port, and protocol by inspecting the network traffic itself to determine if the incoming/outgoing traffic is malicious. It’s a completely managed, highly-available cloud service that boasts features like threat intelligence and signature-based IDPS. Azure Firewall is Microsoft’s go-to technology to protect workloads on Azure Cloud.
What is Azure NSG?
An Azure Network Security Group (NSG) is a firewall that operates at OSI Layers 3 and 4 to filter ingress and egress traffic from resources on an Azure Virtual Network (vNET).
Unlike Azure Firewall, which monitors all traffic for workloads, NSG is commonly deployed for individual vNets, subnets, and network interfaces for virtual machines to refine traffic. It does so by activating a rule (allow or deny) or Access Control List (ACL), which allows or denies traffic to Azure resources.
Azure Firewall vs. NSG
Azure Firewall and NSG are both security services offered by Azure. They both operate by securing traffic based upon a set of rules. However, that is where the similarity ends. While NSG is a classic firewall, Azure Firewall offers next-generation firewall capabilities such as packet inspection and intrusion detection.
Azure Firewall vs. NSG: Overview
The table below details some of the key similarities and differences between Azure Firewall and Azure NSG.
| Azure Firewall | Network Security Group | |
|---|---|---|
| Description | Managed, highly available, robust, and intelligent firewall with advanced packet inspection capabilities | A basic/classic firewall based on a 5-tuple hash |
| Layers of Protection | Offers protection to workloads by inspecting OSI layers 3-7 | Basic traffic filtering at OSI layer 3 and 4 |
| FQDN tag support | Supports FQDN tags | Does NOT support FQDN tags |
| Threat detection and blocking | Supports real-time threat detection | Filters traffic based on allow and block rules |
| Availability Zones | Supports Availability Zones | Does NOT support or require Availability Zones |
| Cost | Starts at $1.25/hour excluding data processing charges | Free, but standard data ingress/egress costs apply |
| Complexity | Requires intermediate to advanced knowledge to configure and implement | Requires basic network knowledge to configure and implement. |
Azure Firewall vs NSG: Features
Azure Firewall is a modern intelligent firewall built to secure the entire workload. Azure Firewall comes in two flavors, standard and premium. Premium offers additional security features.
Key Azure Firewall technology and security features include:
- Protection at OSI layers 3,4 and 7– While traditional rule-based firewalls operate at layers 3 and 4, Azure Firewall works at layers 3, 4 and 7.
- Packet inspection– Azure Firewall intelligently inspects packets and offers protection on the application layer.
- Stateful firewalling– Being a stateful firewall means Azure Firewall continuously analyzes traffic with context. Azure Firewall inspects data packets and runs threat detection by comparing patterns against more than 58,000 signatures available in over 50 categories which are all updated in real-time.
- Threat intelligence-based filtering– Standard version offers L3-L7 filtering and real time threat detection which is directly fed from Microsoft Security Center. Threat intelligence-based filtering compares all inbound/outbound traffic with the blacklist IP addresses to allow or deny traffic. Microsoft updates this blacklist in realtime to safeguard against any potential new attacks.
You can read more about Azure Standard Firewall features in the official documentation.
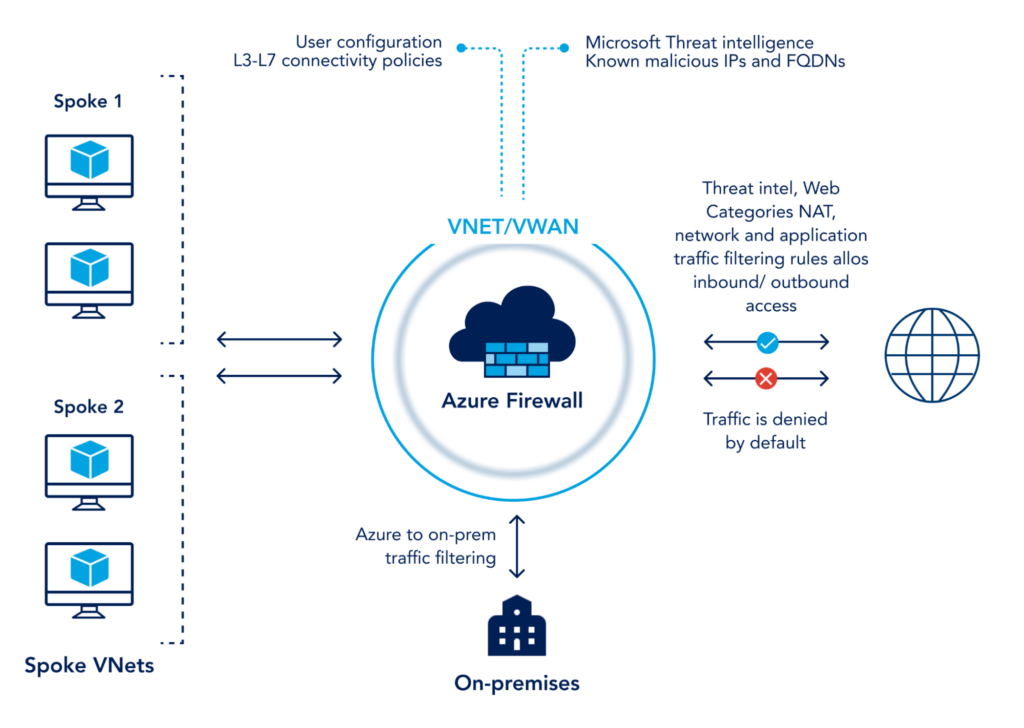
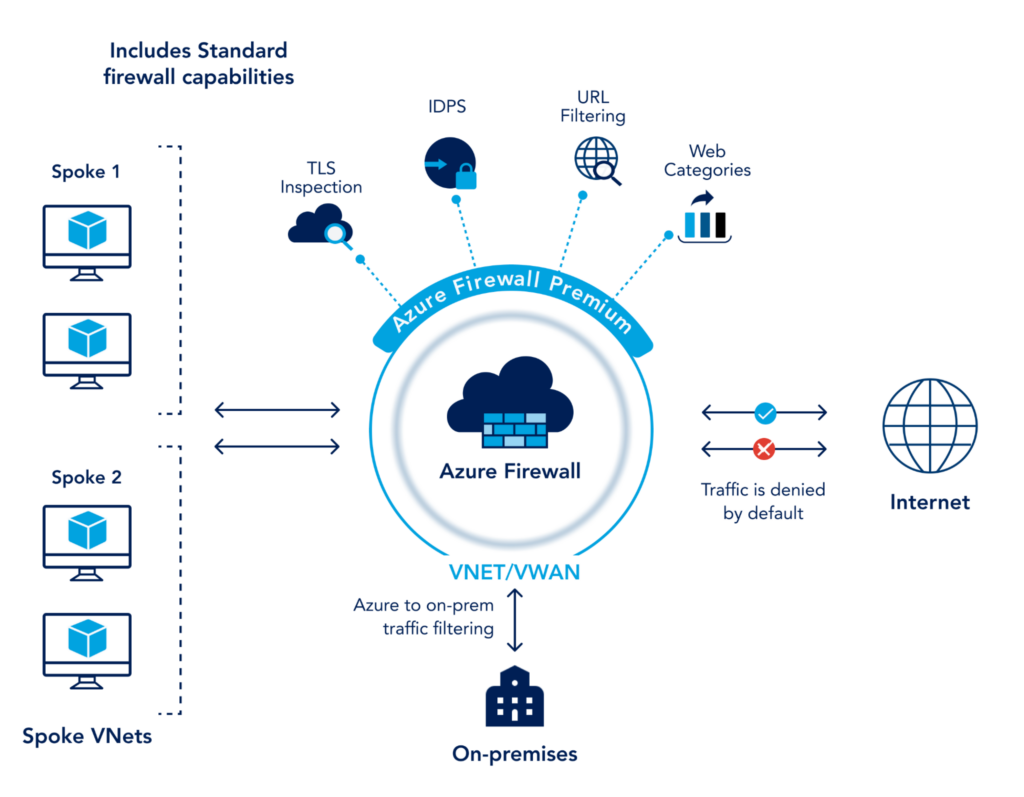
The premium version of Azure Firewall adds additional capabilities such as signature-based IDPS with categories including malware, phishing, coin mining, and Trojan attacks, TLS inspection, and URL filtering.
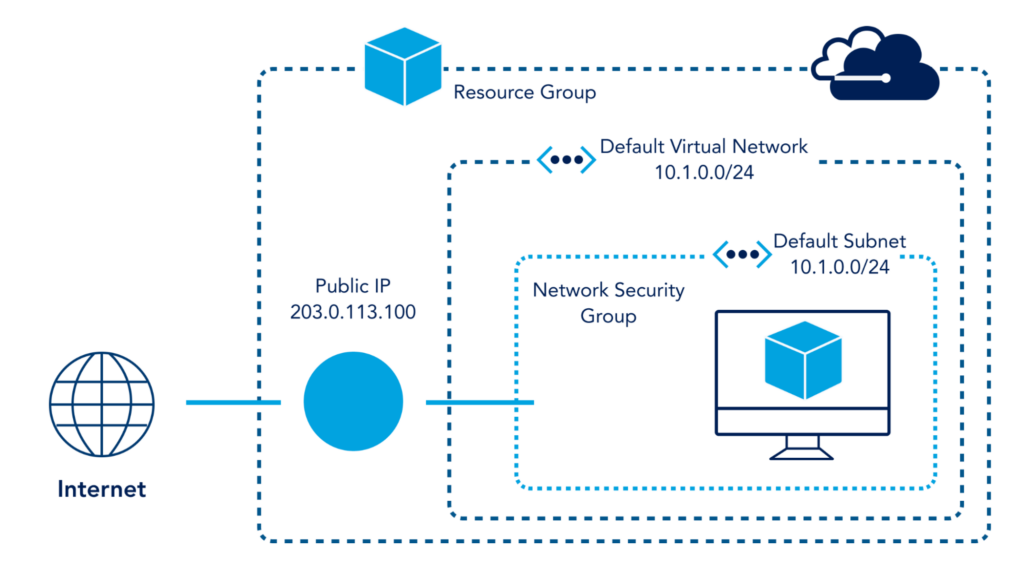
NSG, on the other hand, is an OSI layer 3 and 4 security service. Administrator-defined rules allow or block the traffic based on the 5-tuple hash. A 5-tuple uses five parameters to enforce rules. It includes the IP address for source and destination, the port number for source and destination, and the protocol (TCP/UDP or both).
NSG is created by default with every vNet and virtual machine. You can either create a new NSG or specify an existing NSG while creating the resource. NSG is easy to configure, and the rules work on a priority basis. If an ACL has conflicting rules, the rule with the highest priority (lowest priority number, 100 takes priority over 110) takes precedence.
The image below provides an excellent conceptual breakdown of how Azure NSG features work. The NSG sits inside a subnet filtering all traffic that goes in and out of the subnet. This could also have been implemented on the Default Virtual Network (10.1.0.0/16) or a single VM in the reference image.
Azure Firewall vs. NSG: Use Cases
Azure Firewall is use case-specific. It is not surprising to see a mid-size cloud environment without Azure Firewall as it’s only useful when intelligent threat monitoring is required. For many basic use cases, administrators may feel the cost of Azure Firewall isn’t justifiable.
NSG, on the other hand, is virtually free. For SMBs or a small cloud deployment, where basic network filtering and refinement are required instead of intelligent and real-time threat detection, NSG is the way to go. It can filter your traffic based on allow-or-block rules, is easy to configure, great for creating segments within the network and isolating subnets and vNets, and is virtually free.
Azure Firewall and NSG are Often Used Together
It’s important to note that Azure Firewall and NSG are not mutually exclusive. Almost all cloud deployments will use NSG regardless of using Azure Firewall or not. In fact, Azure Firewall and NSG are often configured in conjunction with one another.
While there are some overlapping functionalities, many use cases require both services. NSG can be used to segregate subnets for different departments and allow access to a management subnet for monitoring and sharing resources like domain controller and file server. Then, an administrator can configure Azure Firewall to inspect incoming traffic from all the end-users over authorized connections. Azure Firewall can also create a highly-available load balancer to ensure the VDI service does not have a single point of failure.
Azure Firewall vs. NSG: Limitations
The limitations of NSG are clear. It is a traditional rule-based firewall that doesn’t offer intelligent features found in many modern security appliances. It provides basic firewalling, but administrators that require more advance features will need an additional solution.
Azure Firewall limitations will vary between SKUs. Below, we’ll review the most important limitations users of each SKU may face.
Azure Firewall Standard SKU Limitations
Key limitations of the Azure Firewall standard SKU are:
- Filtering rules for any other protocols apart from TCP/UDP don’t support Internet-bound traffic. For Internet-bound traffic, administrators can only create filtering rules for TCP and UDP.
- The standard load balancer which does not support Source Network Address Translation (SNAT) for IP protocols. SNAT changes the private IP of a source to a public IP. It can also change a source port. The standard SKU doesn’t support SNAT for IP protocols.
- Migration to a new resource group or subscription is not supported. When moving to a new resource or subscription, the firewall instance has to be deleted and re-created in the new locations.
- Initial public IP assignment cannot be removed. Azure Firewall requires a public IP and either creates or asks for an existing public IP at the time of deployment. It also creates the first configuration during the deployment. This configuration cannot be removed. However, a new public IP can be assigned to the configuration if available.
- Availability zones are only configurable during the time of deployment. There is metadata that needs to be written throughout the selected availability zones which are only possible at the time of deployment. This limitation is by design.
- Port 25 is blocked for all SMTP outbound traffic. This is by design and added to enhance security. Authenticated SMTP relays can be configured on port 587, which is secure. This means that any outbound email sent directly to domains like Hotmail, Gmail, Yahoo, etc will not work unless an SMTP relay is configured to use the secure port.
- No support for IPv6. To date, the standard Azure Firewall SKU does not support IPv6.
Azure Firewall Premium SKU Limitations
Key limitations of the Azure Firewall premium SKU are:
- No support for client TLS certificates. Client certificates are used to establish trust between a client (user/endpoint) and the server. An Azure Firewall is designed to renegotiate the connection with the server and has no access to the private key of the client certificate during renegotiating.
- No Availability Zones in the Southeast Asia (SEA) region. To date, the premium Azure Firewall SKU does not support Availability Zones in the SEA region.
- TLS 1.3 is only partially supported. Currently, TLS tunnels from client to firewall are based on TLS 1.2. Connections from Azure Firewall to the external web server use TLS 1.3.
For a complete list of known issues for both standard and the premium SKUs, review this section of the Azure documentation.
Conclusion
Azure Firewall and NSG are both security service offerings from Microsoft. The question isn’t whether to use Azure Firewall or NSG, but how to effectively use each service. They are often used together to create a secure environment. The decision to use either comes down to the use case and security design. Factors like cost, expertise and overall requirements play a significant role in decision-making.
If securing the network by allowing or blocking traffic on the network layer is your only requirement, NSG is the way to go. Its low cost, limited complexity, and ease of management make it an ideal choice. For more advanced requirements, Azure Firewall is usually the right choice.
You like our article?
Follow our monthly hybrid cloud digest on LinkedIn to receive more free educational content like this.